First off, I want to wish you a happy and prosperous 2024. A big thanks to
and for their time in running the newsletter launchpad, which kick-started newsletters for many.This week, our focus is on Sherlock, an open source reconnaissance tool used to collect information or intelligence about a target, commonly for security or information gathering purposes. I'll delve into the code, highlight interesting aspects and share my ideas to enhance it. Along the way, you'll pick up a few Python tricks and have an opportunity to contribute to the tool.
Let's get started! We'll cover
Sherlock's repository
A reconnaissance related quote
Sherlock’s repository
I have a deep interest in espionage and spy craft movies and podcasts. Right before the year-end hustle, I was engrossed in a podcast called Darknet Diaries by Jack Rhysider. In one episode, Jack interviews a highly decorated CIA case officer. If you're intrigued, give it a listen here.
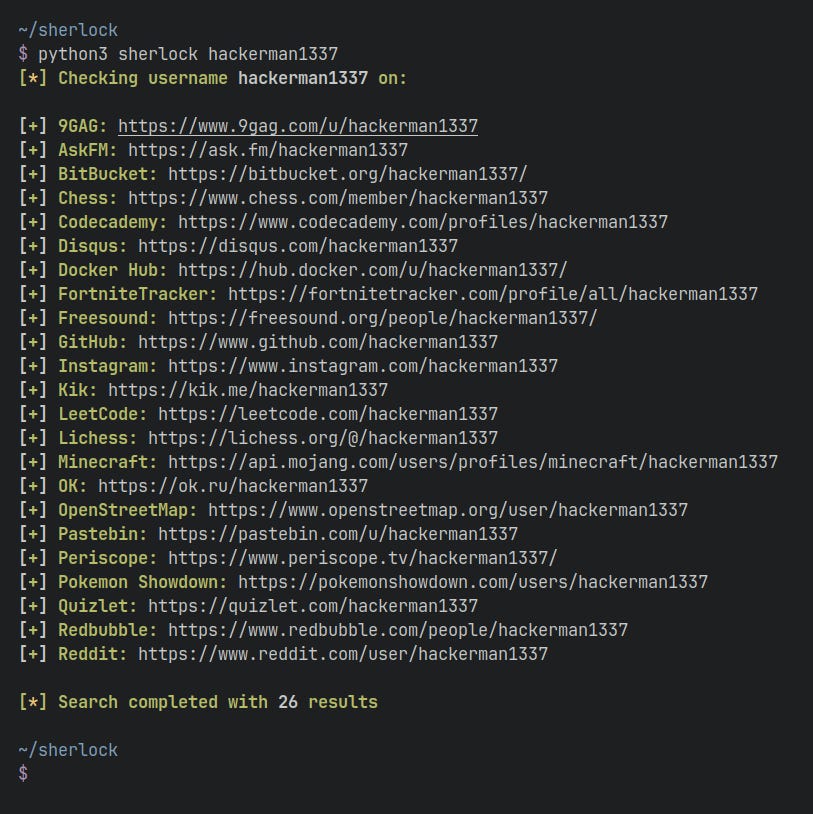
This particular episode sparked the idea for my writing this week. Security researchers invest significant time gathering information about their target, paying attention to even the smallest details. Sherlock comes into play by helping locate social media accounts based on a username across various social networks. It's a handy tool for checking if username(s) are present on any social media sites.
The repo: Sherlock
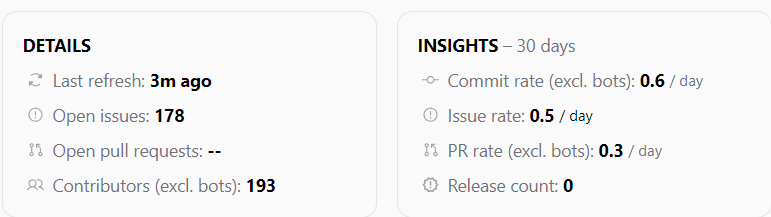
The tool is crafted in Python and as I delved into the code, I stumbled upon some intriguing aspects that I'll share shortly. The repository is buzzing with contributions, indicating that the community actively employs it for security research. Here's a quick snapshot of the open-source contributions.
While examining the code, I observed that the functionality is crafted with straightforward and easily understandable logic. Let's delve into three files in the code base for a few key aspects.
Sherlock.py : The code in this section is pretty sophisticated. It can check if a username exists across multiple social media sites concurrently, making things faster. It's privacy-aware too, supporting Tor for anonymous requests. The code dynamically adapts to each site's needs, using different request methods and error checks. It measures response times, keeping you informed about the performance of the queries. Plus, it cleverly handles errors and notifies you about the progress. The results come back in a neat dictionary, giving you a comprehensive view of the username's presence on various platforms. Those eager to explore innovative Python implementations, this could be a great code snippet to pick up a few cool tricks!
Sites.py : This code efficiently manages information for different social media sites using classes. It loads data from JSON files or URLs, handles errors, and utilizes the requests library, creating a robust framework. This organized toolkit makes it easy to gather and manage diverse website details, including URLs, username formats, and safety status. It's a smart and effective way to keep things neat!
Result.py : This code aids in checking if a username exists on various social media sites. It employs a structured approach to express the results of these checks, providing additional information such as the time it took for the search and any specific details about the result.
Probable enhancements:
While the tool is widely embraced by the ethical hacking community, there are a couple of opportunities for contributions from tool developers in the open-source community.
Progress Monitoring Feature : There is room to enhance the tool by including a feature to monitor the progress of ongoing queries, especially when dealing with a large number of usernames or sites.
This improvement could involve updating the code to maintain a count of completed queries and presenting a visual representation, like a progress bar, to indicate the overall progress. These modifications would offer users real-time feedback on the search status, enhancing transparency and user-friendliness, particularly in scenarios involving numerous usernames or sites.
Advanced Search Capability : Another potential improvement is enabling users to conduct more advanced searches, such as seeking variations of a username or utilizing regular expressions.
To implement this, a new attribute or method that allows users to specify a search pattern could be introduced. This could take the form of a regular expression or a wildcard pattern. When querying usernames, the specified pattern would be applied to match variations or specific patterns, adding versatility to the search process.
These enhancements would add spice to an already powerful tool.
By the way,
recently wrote an article drawing parallels between Sherlock Holmes' case-solving methods and chaining promises in Javascript. You can read it here.A reconnaissance related quote
"The art of war teaches us to rely not on the likelihood of the enemy not coming, but on our readiness to receive him; not on the chance of his not attacking, but rather on the fact that we have made our position unassailable." - Sun Tzu
The quote encourages a proactive and strategic mindset, emphasizing that success comes not from passively hoping for the best but from actively preparing and securing one's position. This principle is applicable not only in traditional warfare but also in the digital realm, where reconnaissance and information gathering play a critical role in cyber-security and risk management.
This brings an end to this article and I welcome your candid feedback on the format and content. If you liked what you read, please do not hesitate to share and spread the love.
Have a fun filled new year, cheers!
–Krish





Krish, after you deduce and explain the code from open source repos, it becomes ‘Elementary!’
I am gonna try this tool, it looks so interesting.
If Sherlock had to quote Git Checkout, he would’ve said
‘What one can invent another can discover’
Thanks for the mention and keep discovering interesting stuff.